I really like the newer event log model on Windows 2008 family, and the flexibility of the XML events and the queries that makes possible.
Recently, I started noticing a quiet failure of a scheduled task. The Task Scheduler thinks that the task completed successfully, though the executable called by the task action returned an error code of 3:
Task Scheduler successfully completed task “\ShareVol_Sync” , instance “{92ac3257-f52d-47eb-9a3a-ce02c5196bbd}” , action “diskshadow.exe” with return code 3.
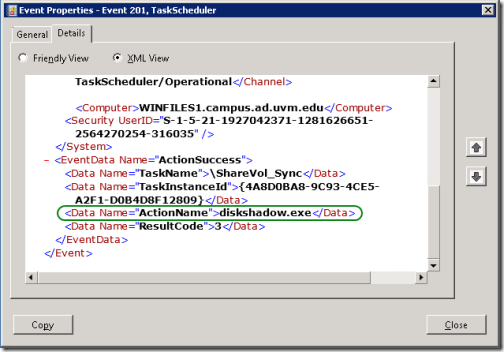
I wanted to see how long this have been going on, so I switched from the Task Scheduler console to Eventlog Viewer, and navigated to the Operational log under “Applications and Services Logsâ€- Microsoft – Windows – TaskScheduler.
I started by using the using the Filter Current log dialog to select events with Event ID 201, but this included all “Action completed†events for all tasks. So I looked at the XML view for one of the events for the task I was researching. The event includes a data value named “ActionName†with the value “diskshadow.exe†that should allow me to find all the relevant events.
Next, I needed to refine my filter to look for this value in the events. I opened the Filter Current log dialog again, and switched to the XML tab, then checked the Edit query manually option. You get a scary warning about not being able to use the GUI again, but that only applies to the current filter. Be bold: click OK.
Next, I edited the query, following examples from this excellent Ask the Directory Services Team blog post. The query is junk the between the select tags. Originally, the query was simply:
*[System[(EventID=201)]]
To that, I added the following:
and
*[EventData[Data[@Name=’ActionName’] and (Data=’diskshadow.exe’)]]
So that the whole query looks like this:
<QueryList>
<Query Id="0" Path="Microsoft-Windows-TaskScheduler/Operational">
<Select Path="Microsoft-Windows-TaskScheduler/Operational">
*[System[(EventID=201)]]
and
*[EventData[Data[@Name='ActionName'] and (Data='diskshadow.exe')]]
</Select>
</Query>
</QueryList>
Now event viewer shows me only the “Action Completed†events for the diskshadow.exe command, and I can see exactly when the behavior changed.
Note that you can save use the query XML with PowerShell’s Get-WinEvent commandlet’s -filterXML parameter [See an example]. You can also use the Save Filter to Custom View option to make this view persistent.
I routinely review Windows’ Event logs during diagnostics and troubleshooting. I find the ability to query those logs for specific data is an indispensable technique. No more dumping to CSV and running findstr! I hope you find it helpful, too.