This post and this twitter thread describe a mechanism to prevent the latest ransomware cyber attack from running. It involves creating 1 (or 3) files with a specific name(s) and with the Read-only attribute set. Although the instructions on the first post describe copying and renaming notepad.exe, any file, even an empty file, with the correct names and the Read-only attribute will suffice, if I read the twitter thread correctly.
There are numerous ways to accomplish this in a large organization, including an SCCM package that either deploys some files, or that runs a script to create the files. However, I decided to use Group Policy File Preferences to copy a small text file to the three filenames described, including setting the Read-only attribute.
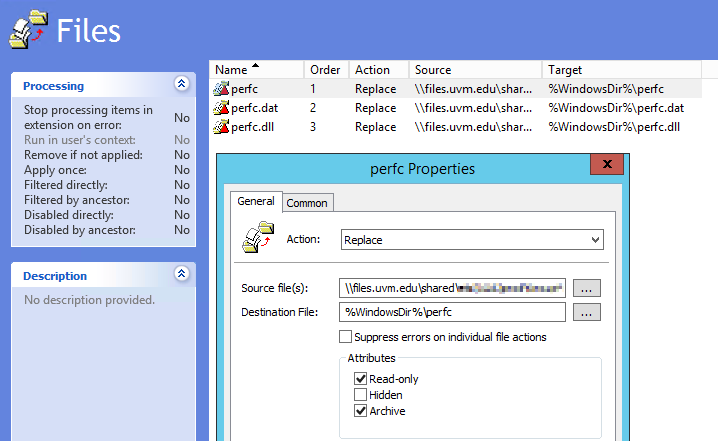
This should be executed on the affected computers at their next GP refresh, which might be sooner than a reboot for a start-up script.