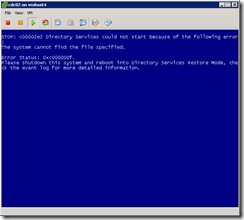
 During an upgrade of our VMware ESX infrastructure, I ran into an issue with our domain controllers. As part of the process we needed to upgrade the virtual hardware that is part of the guest vm. After updating the domain controller guest’s VMware Tools software, I shut down the guest and select Upgrade virtual hardware. Things looked good, so then I powered on the guest and it started to boot. After a moment, it threw a quick bluescreen and auto-rebooted.
During an upgrade of our VMware ESX infrastructure, I ran into an issue with our domain controllers. As part of the process we needed to upgrade the virtual hardware that is part of the guest vm. After updating the domain controller guest’s VMware Tools software, I shut down the guest and select Upgrade virtual hardware. Things looked good, so then I powered on the guest and it started to boot. After a moment, it threw a quick bluescreen and auto-rebooted.
My first order of business was to change the auto-reboot option so I could actually see the error message. I know now that I could just hit F8 during the boot process. However, I did it the hard way.
I booted to the Windows 2008 install media, and ran regedit from the recovery environment. I loaded the HKLM hive, and set the HKLM\SYSTEM\CurrentControlSet\Control\CrashControl\AutoReboot DWORD value to 0 (zero). I see in the KB 307973 article that there’s also a wmic command that will set the option. I don’t know if wmic is available in the WinPE recovery mode.